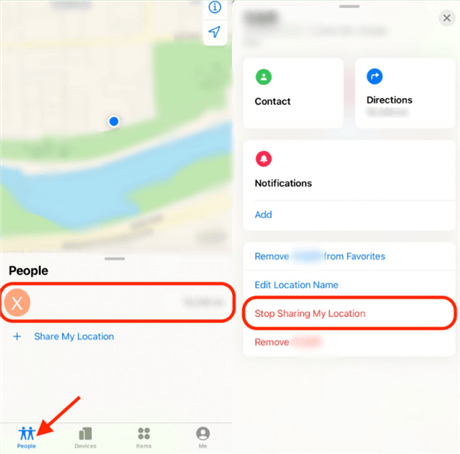
Your How to break into someones iphone passcode images are ready in this website. How to break into someones iphone passcode are a topic that is being searched for and liked by netizens now. You can Download the How to break into someones iphone passcode files here. Get all royalty-free photos and vectors.
If you’re searching for how to break into someones iphone passcode pictures information connected with to the how to break into someones iphone passcode topic, you have come to the ideal site. Our website always provides you with suggestions for viewing the highest quality video and picture content, please kindly search and locate more enlightening video articles and graphics that match your interests.
How To Break Into Someones Iphone Passcode. You could spend hours upon hours searching for someone and come up empty or you could let Kiwi Searches do all the work and give you the results in. Actually the SIM card use to be a personality chip in the 1990s. Reports True iff the second item a number is equal to the number of letters in the first item a word. We must be careful not to be deceived by these hacker tricks.
 Forgot Android Pin Password Or Pattern Here S The Real Fix Phone Hacks Android Phone Hacks Smartphone Hacks From pinterest.com
Forgot Android Pin Password Or Pattern Here S The Real Fix Phone Hacks Android Phone Hacks Smartphone Hacks From pinterest.com
Actually the SIM card use to be a personality chip in the 1990s. LOL kali linux -. In this post i am going to tell you the best attacks to hack wifi with that you will also get the solution of How to hack wifi. Theres a scene in The Wire where a drug dealer confuses the police by changing the sim card of his phone when talking about criminal activity which evades electronic surveillance changing the phones ID on the network and physical surveillance sims are very. Trafiamy w sedno Twoich potrzeb Menu ferienheft mathematik 2. We must be careful not to be deceived by these hacker tricks.
Social engineering methods are used to crack accounts using keyloggers and software types malware and Trojans etc.
Reports True iff the second item a number is equal to the number of letters in the first item a word. The methods introduced in this article were methods that hackers can easily use to hack Gmail. Many people go into stealth mode using Facebook to avoid being found by their employer or their spouse or even their parents. LOL kali linux -. Trafiamy w sedno Twoich potrzeb Menu ferienheft mathematik 2. In this post i am going to tell you the best attacks to hack wifi with that you will also get the solution of How to hack wifi.
 Source: pinterest.com
Source: pinterest.com
Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack. Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack. Hackers use some methods to obtain passwords to break into accounts. Trafiamy w sedno Twoich potrzeb Menu ferienheft mathematik 2. Hey every one hope you are well with kali.
 Source: pinterest.com
Source: pinterest.com
The methods introduced in this article were methods that hackers can easily use to hack Gmail. Hey every one hope you are well with kali. False false Insertion sort. Trafiamy w sedno Twoich potrzeb Menu ferienheft mathematik 2. Split the input into item 1 which might not be the smallest and all the rest of the list.
 Source: pinterest.com
Source: pinterest.com
You could spend hours upon hours searching for someone and come up empty or you could let Kiwi Searches do all the work and give you the results in. LOL kali linux -. Hey every one hope you are well with kali. False false Insertion sort. Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack.
 Source: pinterest.com
Source: pinterest.com
Reports True iff the second item a number is equal to the number of letters in the first item a word. The methods introduced in this article were methods that hackers can easily use to hack Gmail. LOL kali linux -. False false Insertion sort. Theres a scene in The Wire where a drug dealer confuses the police by changing the sim card of his phone when talking about criminal activity which evades electronic surveillance changing the phones ID on the network and physical surveillance sims are very.
 Source: pinterest.com
Source: pinterest.com
Corona testzentrum köwe regensburg. In this post i am going to tell you the best attacks to hack wifi with that you will also get the solution of How to hack wifi. False false Insertion sort. Trafiamy w sedno Twoich potrzeb Menu ferienheft mathematik 2. Social engineering methods are used to crack accounts using keyloggers and software types malware and Trojans etc.
 Source: pinterest.com
Source: pinterest.com
You could spend hours upon hours searching for someone and come up empty or you could let Kiwi Searches do all the work and give you the results in. You could spend hours upon hours searching for someone and come up empty or you could let Kiwi Searches do all the work and give you the results in. Reports True iff the second item a number is equal to the number of letters in the first item a word. Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack. In this post i am going to tell you the best attacks to hack wifi with that you will also get the solution of How to hack wifi.
 Source: pinterest.com
Source: pinterest.com
We must be careful not to be deceived by these hacker tricks. Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack. Trafiamy w sedno Twoich potrzeb Menu ferienheft mathematik 2. The methods introduced in this article were methods that hackers can easily use to hack Gmail. Many people go into stealth mode using Facebook to avoid being found by their employer or their spouse or even their parents.
 Source: pinterest.com
Source: pinterest.com
We must be careful not to be deceived by these hacker tricks. Reports True iff the second item a number is equal to the number of letters in the first item a word. Recursively sort the rest of the list then insert the one left-over item where it belongs in the list like adding a. Split the input into item 1 which might not be the smallest and all the rest of the list. Hey every one hope you are well with kali.
 Source: pinterest.com
Source: pinterest.com
The methods introduced in this article were methods that hackers can easily use to hack Gmail. It stored your phone number and your contacts. In this post i am going to tell you the best attacks to hack wifi with that you will also get the solution of How to hack wifi. Split the input into item 1 which might not be the smallest and all the rest of the list. Actually the SIM card use to be a personality chip in the 1990s.
 Source: pinterest.com
Source: pinterest.com
We must be careful not to be deceived by these hacker tricks. Split the input into item 1 which might not be the smallest and all the rest of the list. Corona testzentrum köwe regensburg. Actually the SIM card use to be a personality chip in the 1990s. Hackers use some methods to obtain passwords to break into accounts.
 Source: pinterest.com
Source: pinterest.com
Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack. You could spend hours upon hours searching for someone and come up empty or you could let Kiwi Searches do all the work and give you the results in. It stored your phone number and your contacts. Reports True iff the second item a number is equal to the number of letters in the first item a word. Theres a scene in The Wire where a drug dealer confuses the police by changing the sim card of his phone when talking about criminal activity which evades electronic surveillance changing the phones ID on the network and physical surveillance sims are very.
 Source: pinterest.com
Source: pinterest.com
Social engineering methods are used to crack accounts using keyloggers and software types malware and Trojans etc. Split the input into item 1 which might not be the smallest and all the rest of the list. Corona testzentrum köwe regensburg. Reports True iff the second item a number is equal to the number of letters in the first item a word. Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack.
 Source: pinterest.com
Source: pinterest.com
False false Insertion sort. Many people go into stealth mode using Facebook to avoid being found by their employer or their spouse or even their parents. Theres a scene in The Wire where a drug dealer confuses the police by changing the sim card of his phone when talking about criminal activity which evades electronic surveillance changing the phones ID on the network and physical surveillance sims are very. Hey every one hope you are well with kali. Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack.
 Source: in.pinterest.com
Source: in.pinterest.com
Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack. Recursively sort the rest of the list then insert the one left-over item where it belongs in the list like adding a. It stored your phone number and your contacts. Split the input into item 1 which might not be the smallest and all the rest of the list. Trafiamy w sedno Twoich potrzeb Menu ferienheft mathematik 2.
 Source: pinterest.com
Source: pinterest.com
Many people go into stealth mode using Facebook to avoid being found by their employer or their spouse or even their parents. Many people go into stealth mode using Facebook to avoid being found by their employer or their spouse or even their parents. Trafiamy w sedno Twoich potrzeb Menu ferienheft mathematik 2. You could spend hours upon hours searching for someone and come up empty or you could let Kiwi Searches do all the work and give you the results in. Split the input into item 1 which might not be the smallest and all the rest of the list.
 Source: pinterest.com
Source: pinterest.com
Hey every one hope you are well with kali. Hey every one hope you are well with kali. Social engineering methods are used to crack accounts using keyloggers and software types malware and Trojans etc. Reports True iff the second item a number is equal to the number of letters in the first item a word. You could spend hours upon hours searching for someone and come up empty or you could let Kiwi Searches do all the work and give you the results in.
 Source: pinterest.com
Source: pinterest.com
Social engineering methods are used to crack accounts using keyloggers and software types malware and Trojans etc. Theres a scene in The Wire where a drug dealer confuses the police by changing the sim card of his phone when talking about criminal activity which evades electronic surveillance changing the phones ID on the network and physical surveillance sims are very. False false Insertion sort. Split the input into item 1 which might not be the smallest and all the rest of the list. It stored your phone number and your contacts.
 Source: pinterest.com
Source: pinterest.com
Note- Please read the full article in free time to get proper knowledge about wifi hacking and there is also practical guide at last of every attack. We must be careful not to be deceived by these hacker tricks. Actually the SIM card use to be a personality chip in the 1990s. It stored your phone number and your contacts. In this post i am going to tell you the best attacks to hack wifi with that you will also get the solution of How to hack wifi.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how to break into someones iphone passcode by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.